Future Horizons:
10-yearhorizon
The notion of personal identity mutates
25-yearhorizon
Establishing and protecting identity becomes routine
This will mean consideration of indirect insecurities, such as LGBTQ+ people being unwillingly identified because of data-sharing leading to openly targeted advertising,4 doxing5 or even physical attacks. Identity security relies on data policies and software routines as well as on “unlinkability”6 and secure hardware implementations such as “secure enclaves”. It is likely that unlinkability will allow people to maintain several legitimate identities simultaneously, for example. Multifactor authentication is used now, but its importance is likely to grow, with distributed and independent issuers of factors making identity theft much harder than it is today.
Reliable means of establishing identity will be key as autonomous agents begin to augment people in certain decision-making scenarios. These agents will need their own identities that are securely linked to their owners. This kind of distributed decision-making raises broader issues about the way human identity will evolve in future. What’s more, establishing the identity of machines is an important issue for the “internet of things”,7 which consists of devices with limited power, network and computational ability. Identity in this context will have to be established by methods that do not rely on strong encryption, network connections and so on. Ensuring that these mechanisms are secure and fit for purpose is an ongoing area of study.
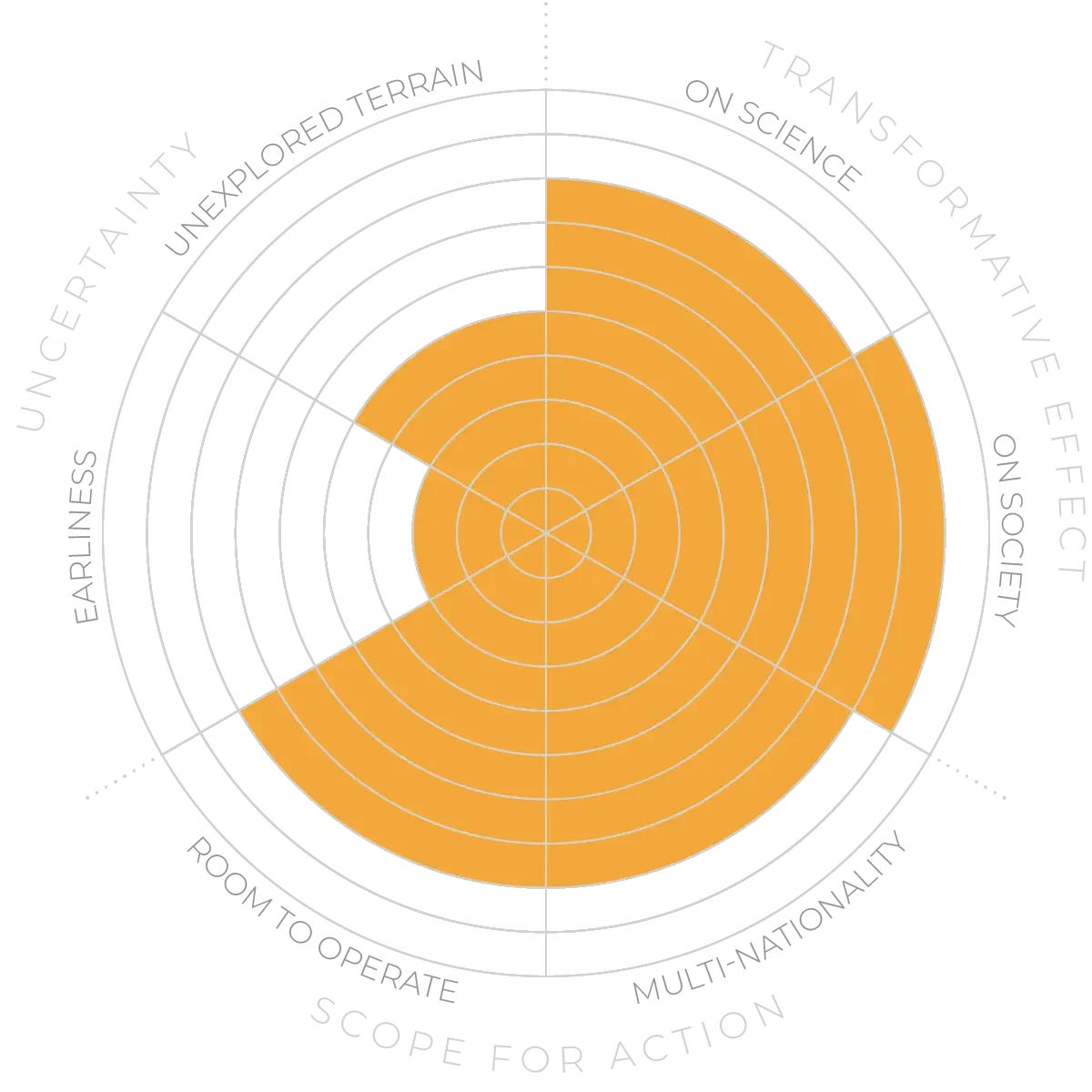
Digital identity - Anticipation Scores
The Anticipation Potential of a research field is determined by the capacity for impactful action in the present, considering possible future transformative breakthroughs in a field over a 25-year outlook. A field with a high Anticipation Potential, therefore, combines the potential range of future transformative possibilities engendered by a research area with a wide field of opportunities for action in the present. We asked researchers in the field to anticipate:
- The uncertainty related to future science breakthroughs in the field
- The transformative effect anticipated breakthroughs may have on research and society
- The scope for action in the present in relation to anticipated breakthroughs.
This chart represents a summary of their responses to each of these elements, which when combined, provide the Anticipation Potential for the topic. See methodology for more information.