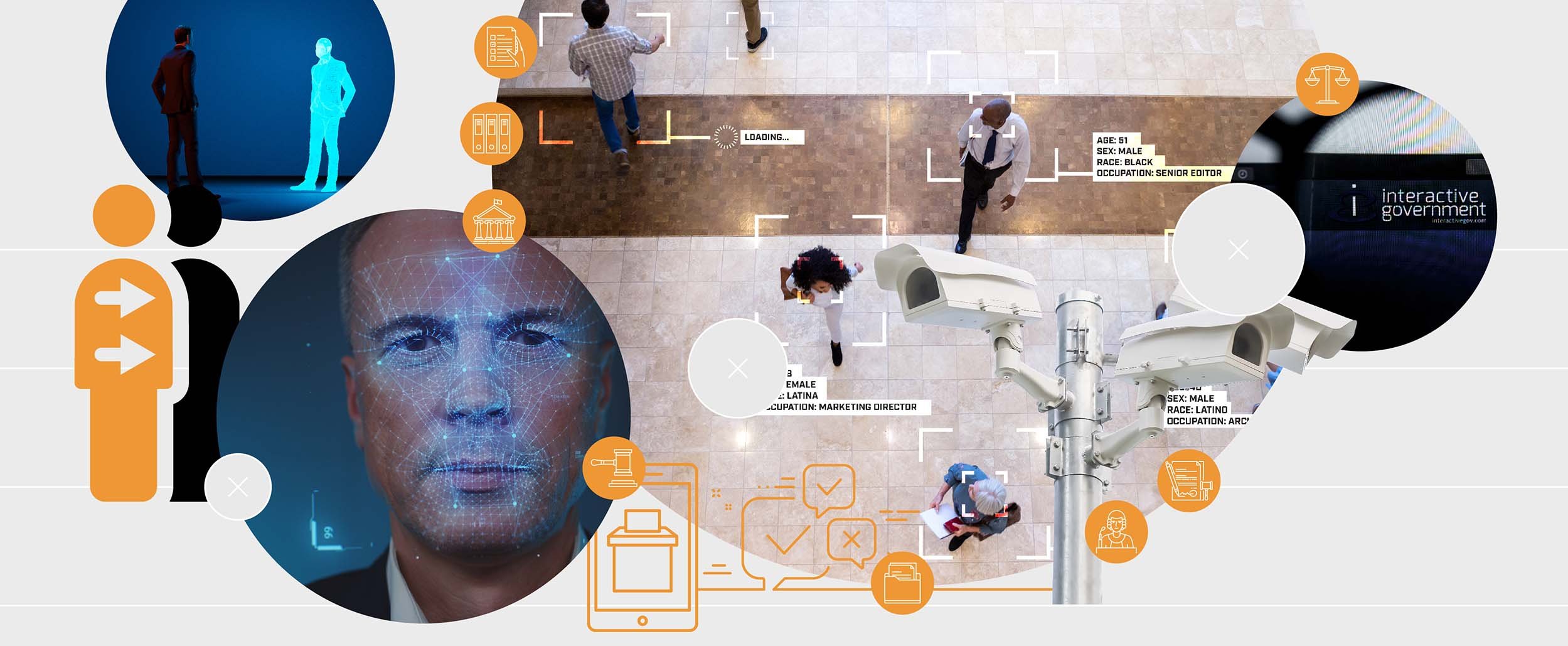
One factor playing an increasingly important role in the processes of democracy is digital technology, which can enhance or diminish it, depending on how it is used. And that raises important questions about the impact and potential of today's technologies and those in the pipeline. Their influence operates at all scales.
At the individual scale is the issue of personal identity in a digital world: how it can be best captured, verified, protected and used. At the scale of communities and societies are digital technologies that can influence the nature of governance and even anticipate and manipulate it. These technologies have the potential to profoundly alter our relationship with democracy in unanticipated ways.
All this sits within a broader debate about the veracity of information, and how to identify and counter misinformation. The ways in which information can and should be moderated is a topic of significant debate, with much agreement that misinformation and hate speech cannot be allowed to spread largely unfettered, as they do today. But moderation must be carefully managed to permit secure, anonymous communication, particularly for whistle blowers and in authoritarian regimes where free speech is stifled.
The decline in global democracy has puzzled many political scientists who have tended to think of democratic change as an ever-increasing process. But recent research has begun to treat democracies as complex systems that are vulnerable to unexpected and unpredictable change.2 Many researchers working in this field are keen to better understand the role that technologies will play in the operation of democratic societies, as well as the philosophies and frameworks necessary for them to be put to best use.
SELECTION OF GESDA BEST READS AND KEY REPORTS:
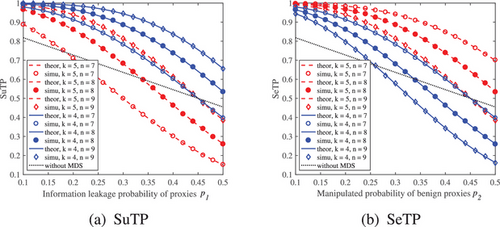
In May 2023, Alexandra Giannopoulou, researcher at the University of Amsterdam, shared Digital Identity Infrastructures: a Critical Approach of Self-Sovereign Identity, which delves into the evolving landscape of digital identity, focusing on the promises and pitfalls of self-sovereign identity systems. While touted as a tool for empowerment, the study warns that its European-wide adoption may inadvertently perpetuate historical identity challenges and place individuals in a vulnerable position. In June, experts from the United States underscored the role of AI in public administration with their work, Catching up with AI: Pushing toward a cohesive governance framework, emphasising the need for unified AI governance. In July, Chinese researchers introduced MDS coding enabled proxy-based Internet censorship circumvention system, revealing a groundbreaking technique for bypassing Internet restrictions through maximum distance separable coding.